
A Journey to the Highest Cybersecurity Maturity: Performance, Part 9 | by Vicente Aceituno Canal | The CISO Den
Activity ManagementPreviously in this series:The inputs of this cycle are:List of Planned Deliverables and Reports
Leading the Digital Revolution

Activity ManagementPreviously in this series:The inputs of this cycle are:List of Planned Deliverables and Reports
Silver Spring, MD, Sept. 19, 2024, CyberNewswire — Aembit, the non-human identity and access management

Universal Robots is planning six demonstrations featuring its collaborative robots at IMTS. | Source: UR
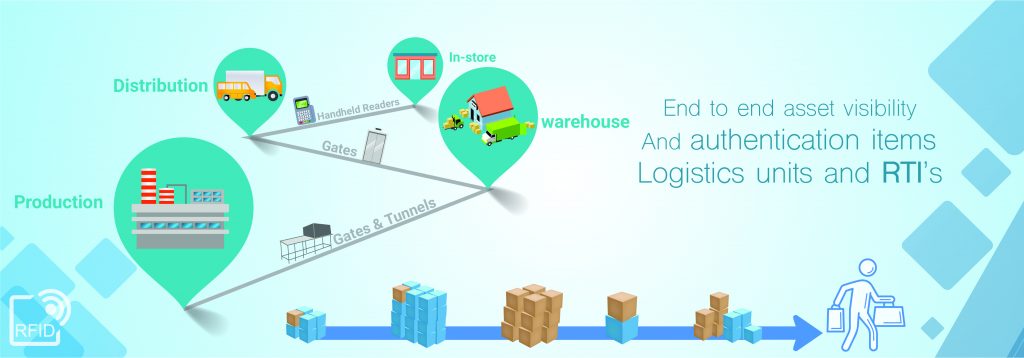
RFID, or Radio Frequency Identification, stands as a pioneering technology that utilizes radio waves to
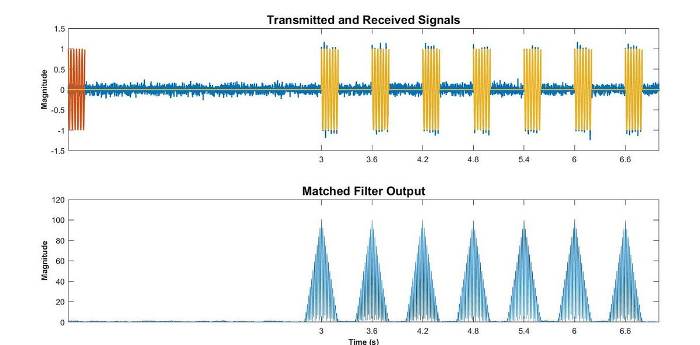
Human eyes can only see in the visible part of the electromagnetic spectrum. Radar (Radio

When developers talk about testing in the software development context, they mostly are not talking
It’s back to school time! Here at Braid Creative we can’t believe how quickly the

Overview The Indian Computer Emergency Response Team (CERT-In) has warned users about five high-severity vulnerabilities

Hi folks,today I’m proud to share another episode of the “Amazing Books Podcast” where my

pH is a logarithmic measurement of the acid or base levels in a substance. It