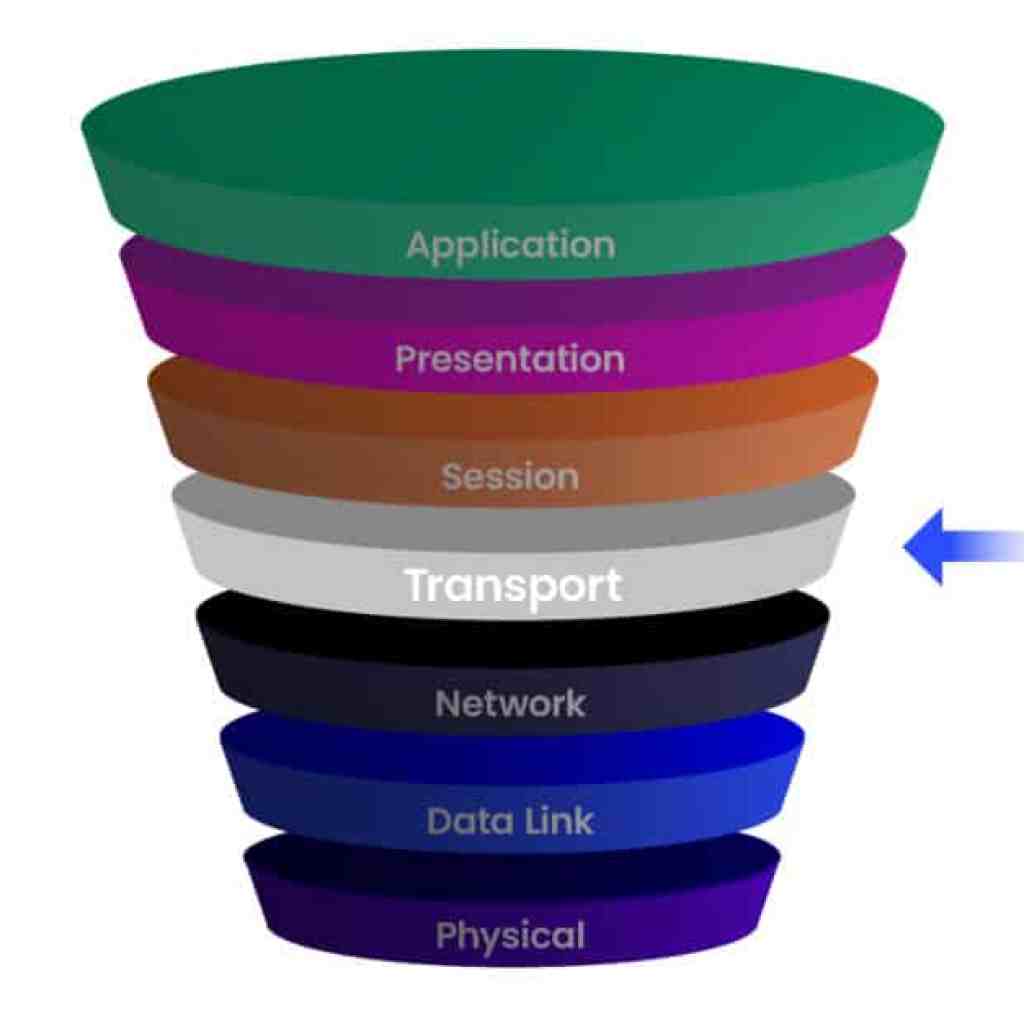
The IT Guide to DDoS: Layer 4 – Everything You Need to Know (Part 2)
This post is part of a series about different types of DDoS attacks. To read
Leading the Digital Revolution

This post is part of a series about different types of DDoS attacks. To read

HomeCybersecurity Lifehacks Cyber Information Gathering: Techniques and Tools for Effective Threat Research To stay safe

Despite global information security spending projected to reach $215 billion in 2024, 44% of CISOs

Recognizing Online Risks

Information and digital security frameworks like FedRAMP, CMMC, and ISO 27001 are not static documents.

By Ravi Srivatsav Everyone knows the cost and frequency of data breaches are rising. The

Many of my readers know me as a cybersecurity expert. More than 12 years of

Cybersecurity Awareness Month – marked each October in many countries – is about working with

Artificial Intelligence (AI) and Machine Learning (ML) are transforming the marketing landscape, enhancing customer engagement,

HomeService UpdatesANY.RUN Now Integrates with Splunk! We have some thrilling news to share with you