
How to Get Threat Intelligence Using TI Lookup Search Parameters
HomeInstructions on ANY.RUNHow to Collect Threat Intelligence Using Search Parameters in TI Lookup ANY.RUN‘s Threat
Leading the Digital Revolution

HomeInstructions on ANY.RUNHow to Collect Threat Intelligence Using Search Parameters in TI Lookup ANY.RUN‘s Threat

If you’re a security professional like me, you’re not used to your function being seen
Like many large-scale network security projects, microsegmentation can seem complex, time-consuming, and expensive. It involves

Business Continuity Management (BCM) has evolved into a sophisticated discipline essential for navigating today’s complex

Cyberbullying: Empowering Families to Safeguard Their Kids

We’ve talked a lot on this blog about protecting controlled unclassified information, and we’ve mentioned
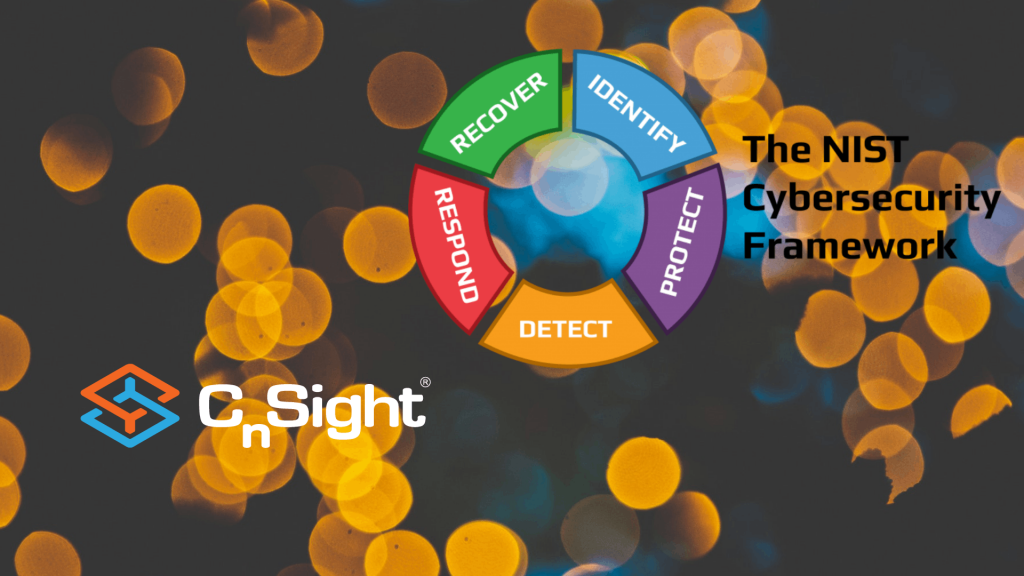
To celebrate Cyber Awareness Month, we’ve been releasing a series of posts outlining ways Cybersecurity
Silver Spring, MD, Sept. 19, 2024, CyberNewswire — Aembit, the non-human identity and access management

Hi folks,today I’m proud to share another episode of the “Amazing Books Podcast” where my
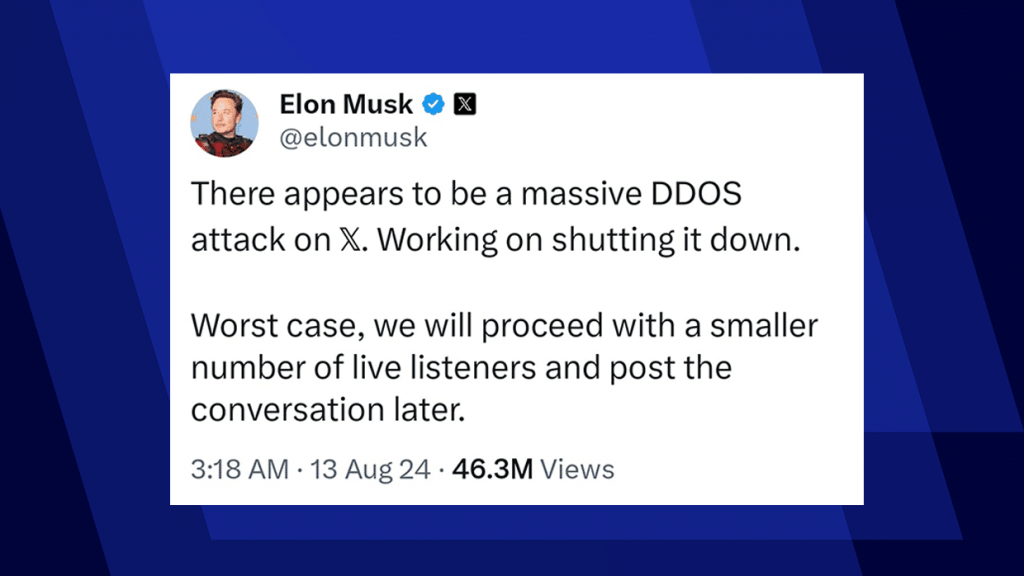
Yesterday, August 12, 2024, the X platform (formerly Twitter) experienced a significant Distributed Denial-of-Service (DDoS)