
Borrowed this title from Software App Development
Borrowed this title from Software App Development Picture a day when you wake up and
Leading the Digital Revolution

Borrowed this title from Software App Development Picture a day when you wake up and

Resistant Privacy: Hardware Level Security With App Lock Ever misplaced your phone? Or let a

Hello Cyber Builder 🖖 This week, we’re diving into one of the most exciting talks

Who should read this? You’re here because you want to learn more about IT audit

BEC, or Business Email Compromise, affects companies of all sizes. After gaining access to or

If you’ve ever sat at your desk wondering what exactly the bunch of outsiders hanging

The below list covers the key professional bodies and certifications to consider as part of

Hello Cyber Builders 🖖 Data is more than just numbers—it’s about making informed decisions. Do

“The only rules that really matter are these: what a man can do and what
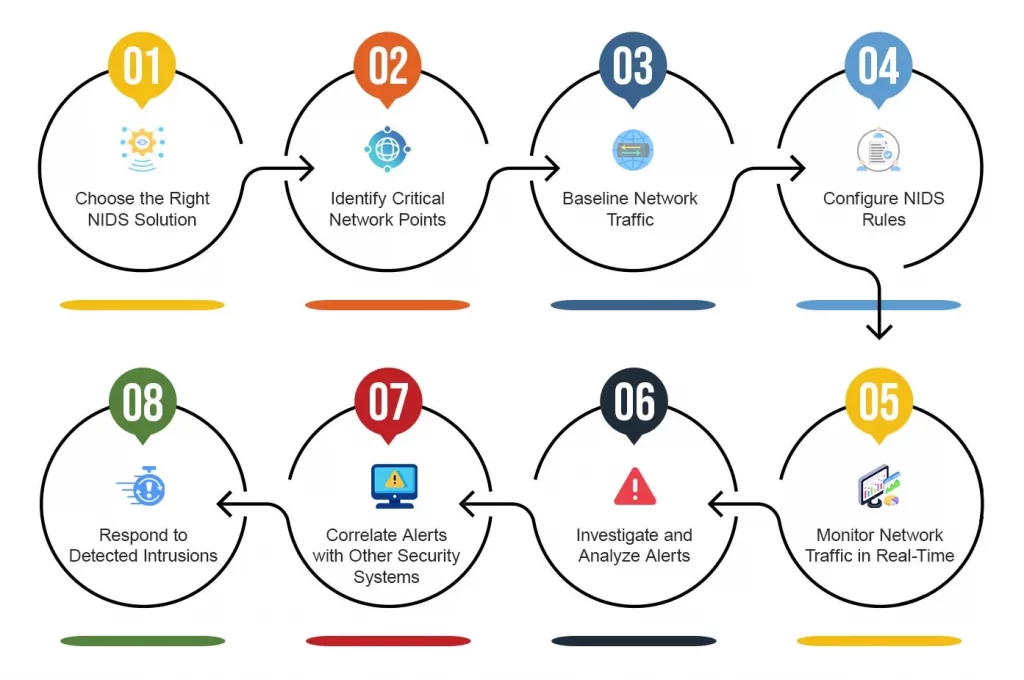
Network based Intrusion Detection System (NIDS) is an important layer of security in the cybersecurity