
Monitoring and Logging Requirements for 2025 Compliance
Let’s face it—getting audit approval is tougher than ever, especially when we consider log monitoring.
Leading the Digital Revolution

Let’s face it—getting audit approval is tougher than ever, especially when we consider log monitoring.

Whenever you’re surfing the internet, every click, search, and scroll leaves behind a small trace

UnderDefense MAXI is on fire! UnderDefense MAXI has garnered an impressive 9 🎉 badges in

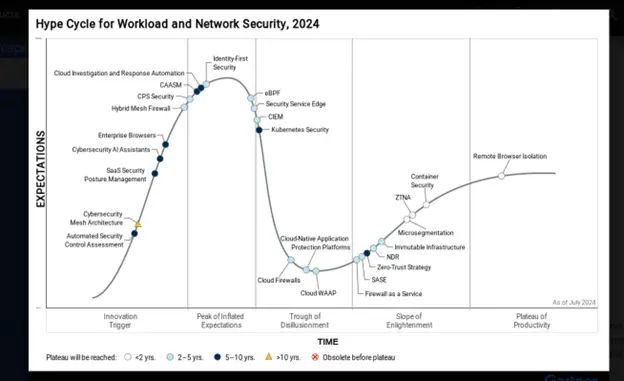
The Network and Information Security Directive, known as NIS2 and effective beginning October 17, 2024,
/*! elementor-pro – v3.22.0 – 24-06-2024 */ @charset “UTF-8″;.entry-content blockquote.elementor-blockquote:not(.alignright):not(.alignleft),.entry-summary blockquote.elementor-blockquote{margin-right:0;margin-left:0}.elementor-widget-blockquote blockquote{margin:0;padding:0;outline:0;font-size:100%;vertical-align:baseline;background:transparent;quotes:none;border:0;font-style:normal;color:#3f444b}.elementor-widget-blockquote blockquote .e-q-footer:after,.elementor-widget-blockquote blockquote

Hello Cyber Builders 🖖 We’re back with another dive into the fascinating dynamics of the
“Security is like an onion: the more layers you add, the harder it is to
This week I attended CSO Online’s CSO Security Summit in London, which was tracked into
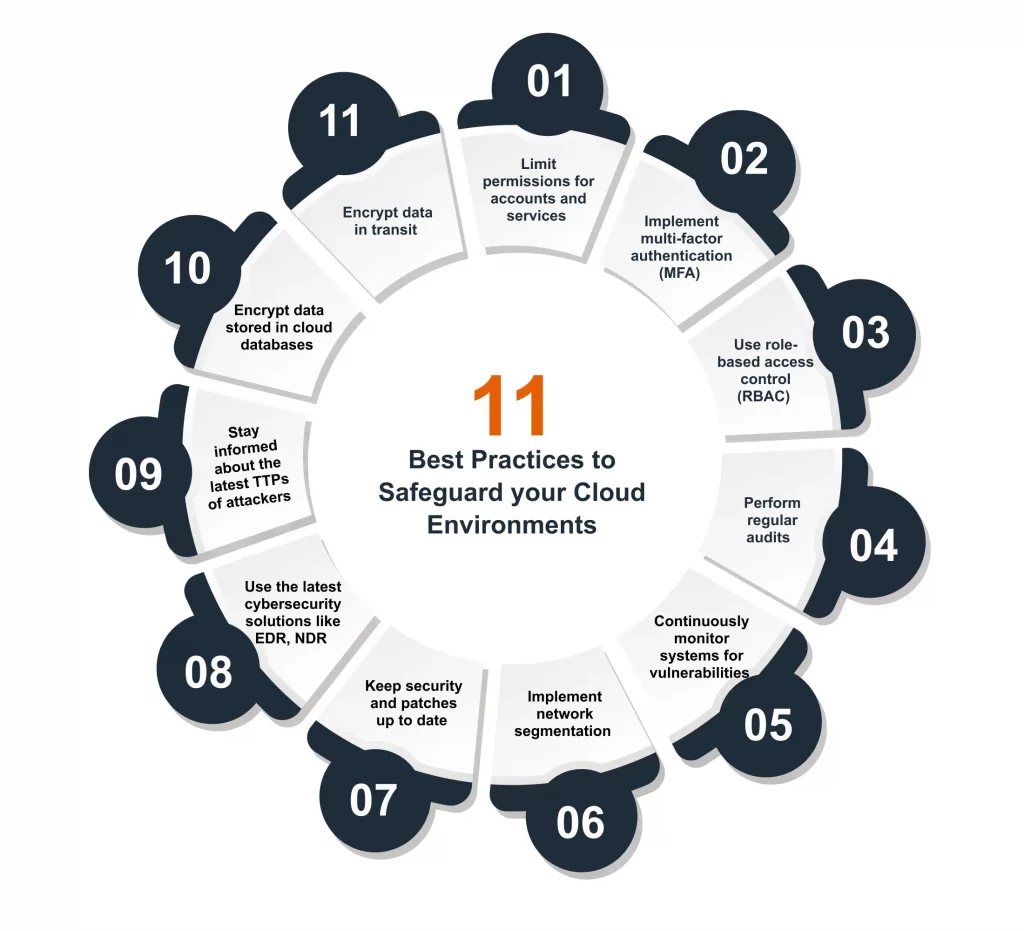
Is your system being used for crypto mining without your consent? This might sound unlikely

As we approach the year-end, prioritizing cybersecurity is essential for businesses to safeguard sensitive information,