“Security is like an onion: the more layers you add, the harder it is to peel through.”
Matthew Sciberras, CISO-VP of Informational Security at Invicti Security
If you’re stepping into the CISO role or taking the first steps in building a cost-effective security stack, here’s some practical, straight-from-the-trenches advice. Building a solid defense doesn’t mean throwing money at every shiny new tool. It’s about picking smart layers of protection that give you the most bang for your buck, starting small and scaling up as your needs (and budget) grow.
From detection to response, let UnderDefense MDR handle it so you don’t have to
What is a Security Stack?
Think of your security stack as the backbone of your defense strategy—a layered set of tools and practices working together to protect your organization. It’s not just about grabbing the latest tech; it’s about building a tailored system that covers all the bases. From endpoint detection and firewalls to SIEMs and threat intelligence platforms, your stack must spot, block, and respond to threats across every corner of your infrastructure.
As a security fan, you know this: the best stack evolves. Threats change, tech advances and your stack should grow with it. Ultimately, it’s not about having every tool but the right tools, fine-tuned and working in harmony. Let’s face it—if your tools don’t play well together, you’re just stacking problems instead of solving them.
What’s shaping (and complicating) CISO’s security stack
Building a strong security stack is about navigating the forces shaping your choices—like compliance demands, evolving threats, and resource constraints. But let’s be real: these same factors often bring their own set of challenges, from integration headaches to budget juggling.
|
Major Stack-Shaping Factors |
Major CISO’s Challenges |
|
1. Compliance frameworks 2. Internal resource allocation: 3. Threat environment dynamics |
1. 2025 Compliance Complexities 2. Internal shortages: 3. AI phishing, deepfake scams, and so on – new headaches |

From battle-tested essentials to cutting-edge innovations, your toolkit should be as dynamic as the challenges it faces.
The current security stack has tools for every threat angle:
- Threat Intelligence Platforms
- Endpoint Detection and Response (EDR)
- Extended Detection and Response (XDR)
- Security Information and Event Management (SIEM)
- Digital Forensics & Incident Response (DFIR)
And there’s more where that came from.

How to build a security stack in 2025
Let’s keep it real—before diving into tools and fancy defenses, you’ve got to know what you’re working with. Map out your assets, document your network, set up solid logging, and get to know your staff. Humans are always the easiest entry point for attackers, and you should never forget that.
So, let’s walk together the essentials, mid-range must-haves, and high-impact tools.
1. Start with the security stack essentials
Alright, first things first. Before we get fancy with advanced tools, let’s set up a strong foundation. These are the budget-friendly, no-brainer moves that can save you a ton of headaches.
- Password management: Seriously, don’t skip this. Get a password manager like LastPass or Bitwarden (around $3-$6 per user/month). Strong, unique passwords are your first line of defense.
- Employee training: Here’s a secret—trained employees are your undercover security agents. Go with KnowBe4 for phishing simulations and security awareness training (about $10 per user/year). It’s worth every penny.
- Basic security signage: Remind people to think before they click. Cheap but effective—just print some posters and stick them by the coffee machine.
2. Affordable & effective defensive must-haves
Don’t forget the cost-effective yet powerful solutions. These aren’t the fanciest tools, but they pack a punch in terms of security value.
- Multi-factor authentication (MFA): An extra login layer with Duo MFA (around $3 per user/month). Simple but effective.
- Vulnerability scanning: Regularly scan for weaknesses with Tenable.io or Qualys (around $2,000 to $5,000 per year).
- Firewall/WAP (Web Application Protection): Basic defenses with Palo Alto Networks or Fortinet firewalls—expect $1,000 to $5,000 for SMB setups.
“In your first year as a CISO, you’re just picking the low-hanging fruit—things like security through obscurity, strong passwords, and basic security training. Whether your budget’s tight or not, these are the fundamentals. But as soon as you’ve got those down—you start layering. Security is like an onion: the more layers you add, the harder it is to peel through.”
Matthew Sciberras, CISO-VP of Informational Security at Invicti Security
3. Layer on core threat detection and prevention
Now we’re talking. These tools won’t break the bank, but they give you a solid defense. Think of them as your early warning system.
- Anti-malware: Go with something reliable like Malwarebytes ($40 per device/year). It’s like a bouncer that keeps the sketchy characters out.
- Intrusion detection system (IDS): To spot shady activity on your network, try Snort (free and open-source) or AlienVault OSSIM if you need more features at a reasonable cost.
- VPN: Encrypt your network traffic. NordVPN Teams or ExpressVPN will do the job (around $7-$8 per user/month).
4. Bring in targeted threat detection and protection
Got a bit more budget? Great, because now we’re moving up to tools that target specific threats. Phishing, ransomware, web-based attacks—they’re all waiting for their moment, so let’s make it tough for them.
- Email filtering: This one’s a must for phishing. Try Mimecast (starts around $3-$4 per user/month). It keeps the junk out and your inbox clean.
- Web Application Firewall (WAF): For web-based attacks, go with Cloudflare WAF (about $20/month) or AWS WAF ($5/month + $1 per million requests).
- Advanced threat detection: When you’re ready for more firepower, look at Palo Alto Networks Cortex XDR or Cisco Talos. They’re not cheap, but they bring powerful threat intelligence to the table.
5. Scale up with strategic, flexible controls
Alright, now we’re getting serious. As your organization grows, you need security that grows with you. This is where flexibility and scale come into play.
- SASE (Security Access Service Edge): Combines networking and security for your remote workforce. Look into Zscaler or Cisco Umbrella (think $20-$30 per user/month). Perfect for the new hybrid work reality.
- Data Loss Prevention (DLP): Control your data like a hawk with Forcepoint DLP or Digital Guardian DLP ($15-$30 per user/month). Keeps sensitive info where it belongs.
- Endpoint Detection and Response (EDR): Keep an eye on endpoints in real time. CrowdStrike Falcon and SentinelOne (starting at $6-$8 per endpoint/month) are solid options.
The EDR tools are great but here’s something we’ve seen far too often—if they aren’t set up or maintained properly solutions quickly turn into alert factory. Managed EDR services cut through the noise, fine-tune the setup and ensure your EDR works the way it’s supposed to—keeping your endpoints safe without driving your team crazy.
6. High-impact, specialized solutions for real-time protection
Here’s where we go all in. These are your high-end, high-stakes tools for 24/7 monitoring and instant response. Perfect for catching what other tools miss.
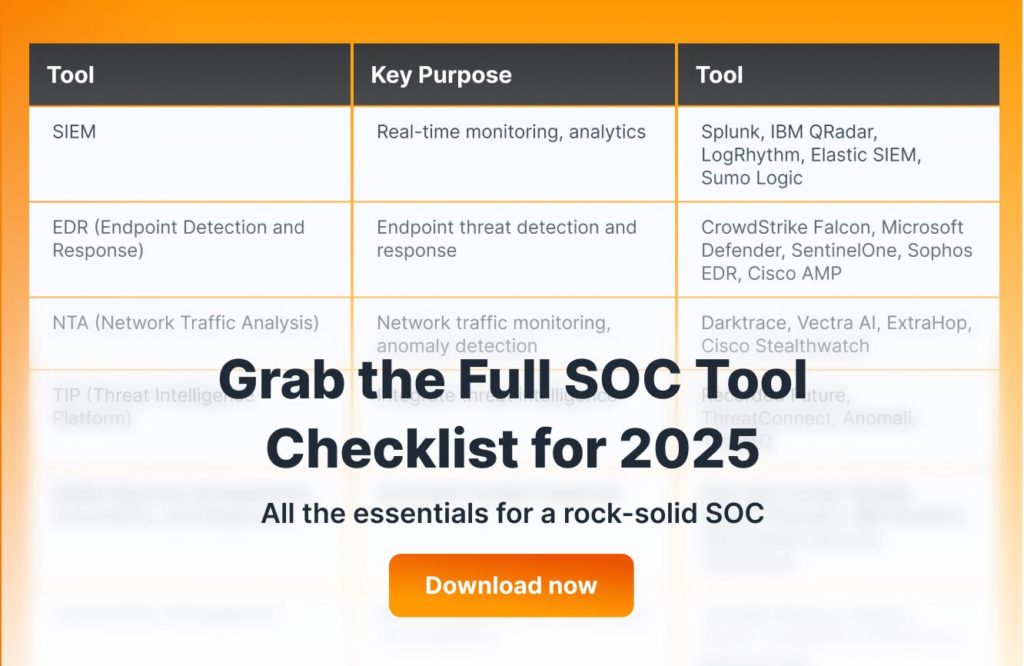
- SIEM (Security Information and Event Management): SIEM is like the brain of your security operations. Consider Splunk (starts around $150 per GB/day) or IBM QRadar for real-time insights.
SIEMs are fabulous, but they’re not always delivering full value—many teams struggle with setup and get buried in alerts. That’s where managed SIEM comes in. With expert fine-tuning, log noise is cut down, critical threats stand out, and your SIEM finally works as it should—not just churning logs, but driving real insights.
Explore the common pricing models for managed SIEM to budget effectively
- Managed detection and response (MDR): MDR usually runs about $15 per endpoint/month, and it’s worth every penny. A good MDR service isn’t just an alert system—it’s a full team of threat hunters blending AI insights with human expertise. You get 24/7 coverage, faster detection, and smarter responses, all without the headache of managing it in-house.
Managed SOC: If you’re not ready to build an in-house SOC, outsourcing is a smart option. SOC services can cost $30,000 to $100,000 per year but provide 24/7 eyes on your systems. Managed SOC offers around-the-clock monitoring and real-time threat response. You get the security of a full SOC without the hassle of hiring, training, and scheduling a team.
“If I had to choose between outsourcing a SOC or going with MDR, I’d pick MDR. It’s often cheaper but just as effective. Plus, MDR gives you more flexibility—custom detection, faster response times, and way less noise in alerts.”
Matthew Sciberras, CISO-VP of Informational Security at Invicti Security
7. Compliance and specialized controls
In 2025 compliance is non-negotiable. High-stakes environments require extra layers to check every box and keep regulators happy.
- Third-party security audits: External audits are like getting a second opinion on your security posture. Firms like Deloitte and PwC can run anywhere from $10,000 to $100,000 per audit.
- Privileged access management (PAM): Focuses on the control, monitoring, and protection of privileged accounts within with tools like CyberArk. Expect $30,000 to $100,000 per year, but it’s worth it for protecting critical assets.
- Identity and access management (IAM): For access control, Okta or Microsoft Azure AD Premium works well at around $6-$10 per user/month.
Here’s where things get simpler: a 24/7 threat protection platform, often called an MDR solution, can take a lot of the compliance weight off your shoulders. It streamlines log monitoring and identity management into one easy-to-manage system. Additionally, you get free compliance templates that make audit prep faster and less painful. And with expert vCISO services, you’ve got the guidance to automate compliance processes and free up your team for the work that truly matters.

Final thoughts: Smart, layered security on a real-world budget
There you have it—my take on building a security stack that balances cost and protection. Let’s not kid ourselves: security isn’t cheap. The global average cost of a breach in 2024 hit $4.88 million—and it’s even worse in the U.S., climbing to $9.36 million. But here’s the thing: every dollar you invest in security is a dollar you’re saving from cleanup costs, legal fees, and lost trust. The key is starting smart. Nail the basics first, then layer on advanced defenses over time. This gives you room to think, choose wisely, and build a fortress—one layer at a time.
UnderDefense is here to help you handle the complex stuff—like SIEM tuning, MDR, and 24/7 SOC coverage—so you can focus on your core mission without the constant firefighting. And remember, security isn’t about having every tool on the market; it’s about having the right tools in the right places.
1. What are Security Stack examples?
Security stacks typically include tools like firewalls, multi-factor authentication (MFA), endpoint detection and response (EDR), and security information and event management (SIEM) systems. For example, you might pair a robust EDR like CrowdStrike with a SIEM such as Splunk, alongside tools for identity management like Okta, and data loss prevention (DLP) systems. Each organization’s stack will vary based on its size, industry, and risk profile.
2. What are Security Stack best practices?
- Start with essentials: MFA, firewalls, and regular vulnerability scans.
- Prioritize integration: Ensure your tools work together seamlessly to avoid gaps.
- Regularly update and fine-tune: Outdated configurations are as risky as no protection at all.
- Train your team: Even the best tools fail without informed users.
- Monitor continuously: Use 24/7 monitoring solutions like managed SOC or MDR to stay proactive.
3. What are Security Stack key components?
At its core, a strong security stack includes:
- Identity and Access Management (IAM): Control who can access what.
- Endpoint Protection (EDR/XDR): Monitor and protect devices in real time.
- Network Security (firewalls, IDS/IPS): Protect the infrastructure.
- Threat Intelligence & SIEM: Correlate and analyze logs for smarter detection.
- Data Protection (DLP): Prevent leaks and ensure sensitive data stays secure.
4. How do I build a Cloud Security Stack?
Start by mapping your cloud assets and understanding their vulnerabilities. Key steps include:
- Deploying cloud-native tools like CSPM (Cloud Security Posture Management) to monitor configurations.
- Adding IAM solutions to control access to cloud services.
- Implementing EDR/XDR for endpoint visibility, even in hybrid environments.
- Setting up network segmentation and firewalls to secure your cloud perimeter.
Relying on managed SOC or MDR services for real-time monitoring and incident response in complex cloud ecosystems.