Let’s face it—getting audit approval is tougher than ever, especially when we consider log monitoring. That’s where this guide comes in. We’ve done the heavy lifting by pulling together the exact logging and monitoring requirements from top standards like SOC 2, FISMA, HIPAA, ISO 27001, PCI DSS, and more. So, instead of experiencing severe headaches researching recent regulations, you have a straightforward and downloadable list of log monitoring requirements across main compliance frameworks.
Here, we don’t just outline the rules; we show you how to build a log monitoring strategy that doesn’t quit when things get messy. Well, frankly speaking, cloud-native tools like Amazon OpenSearch are not a full solution for 24/7 log visibility. How will you ensure log persistence and accessibility even when containers, pods, or nodes fail? Or when on-prem systems lose connectivity? So, let’s make sure you’re ready for any audit and any incident that 2025 might throw your way.
From Log Monitoring to Full Threat Defense


What is log monitoring?
Log monitoring boils down to keeping track of all the digital breadcrumbs your systems leave behind. Every access attempt, system error, or data change creates a “log”—a record of what happened. By monitoring, collecting, and organizing these logs, you’ll have a treasure trove of info to help strengthen your cybersecurity.
So, what are logs?
Logs are like your system’s diary, automatically recording a stream of events over time. They tell you who tried to log in, what systems did when they started, any errors, and changes to your data. Each entry includes details like the time, the user involved, and what went down. Here’s a look at the different types of logs you’ll want to pay attention to:
System Logs
These capture system events, like when it boots up, shuts down, or hits an error. They’re crucial for making sure your system’s healthy. E.g., Startup logs, shutdown logs, and error reports.
Security Logs
These watch over security events, recording things like login attempts and permission changes. They’re key to spotting and preventing issues. E.g., Access logs, authentication checks, and permission changes.
Application Logs
Created by apps to keep tabs on errors and key actions, helping you troubleshoot and optimize performance. E.g.: Error logs, activity logs, and performance stats.
Network Logs
These cover traffic on your network and communication between devices, helping you manage connectivity and security. E.g., Firewall logs, router activity, and access attempts.
Database Logs
Track what’s happening inside your databases, like data changes and access requests, ensuring data stays intact and secure. E.g., Transaction records, error logs, and access logs.
Audit Logs
These are a compliance must-have, documenting changes and reviews for regulatory needs. They’ll back you up during an audit. E.g., Policy updates, configuration changes, and compliance checks.
Event Logs
A general category that includes any significant events in your systems, offering a bird’s-eye view of everything happening. E.g.: System events, security alerts, and network traffic.
Log monitoring benefits for businesses
Log monitoring isn’t something you do to check off a box; it’s a smart move with real daily benefits:
- Improves security: Log monitoring is like having an extra set of eyes on your IT environment. By monitoring 24/7 you can catch anything unusual before it becomes a big problem. Monitoring lets you see threats, vulnerabilities, and strange patterns that might mean an attack is coming.
- Makes compliance easier: Regulations like SOC2, HIPAA, and PCI DSS require you to prove you’re protecting sensitive data. With a good log monitoring system you’re already halfway there—logs keep you audit-ready, help you meet standards, and save you the stress of last-minute record gathering.
- Helps optimize IT: Log analysis isn’t just for security; it can also show you where systems are slowing down or misbehaving. This gives your team the chance to fix issues before they become big problems, keep things running smoothly, and save time.
- Prevents fraud: Logs create a paper trail of activity so if anything suspicious—like unauthorized access or strange transaction—happens you’ll know right away. Catching these issues early protects your bottom line and your reputation.
- Simplifies audits and investigations: When it’s an audit or investigation time logs give you the whole story—what happened, when, and who was involved. This saves back and forth and shows auditors you mean business.
- Speeds up incident response: During an incident, logs give you instant visibility, so your team can respond faster and reduce downtime. They also give you the info you need to improve and learn from any gaps in your response.
Log monitoring and regulatory compliance
Keeping up with log monitoring compliance can be daunting, especially with each framework—NIST CSF, ISO 27001, and PCI DSS—having its own set of rules. But at the end of the day, these regulations are all about creating a security baseline. A good log monitoring setup will keep your data safe and take a lot of the stress out of audit time.
Why compliance programs matter
Compliance programs outline minimum security requirements, covering technical actions (like logging and monitoring) and broader stuff like policies and staff training. These frameworks give you a foundation, but each organization customizes it to their risks and needs.
Who needs to be compliant?
Compliance requirements span across industries. Some, like PCI DSS, are specific to companies that handle payment data, while others, like HIPAA, are focused on healthcare. But sometimes even companies outside of these sectors have to follow certain parts. For example, a company that self-insures their employees might have to follow HIPAA in certain areas.
Common types of compliance regulations
Each compliance program has its own logging and monitoring requirements. Here are a few from our table:
- NIST CSF: Continuous monitoring to catch threats early, whether that’s network activity or third-party actions.
- ISO 27001: Logging daily activities and unexpected events to help identify potential security risks.
- PCI DSS: Any business that handles cardholder data must have strict monitoring and logging to prevent fraud.
Why being compliant pays off
The cost of non-compliance is high. PCI DSS fines can be up to $100,000/month and HIPAA fines can be up to $1.5 million per incident. These penalties are why it’s worth following the compliance schedule and being audit-ready.
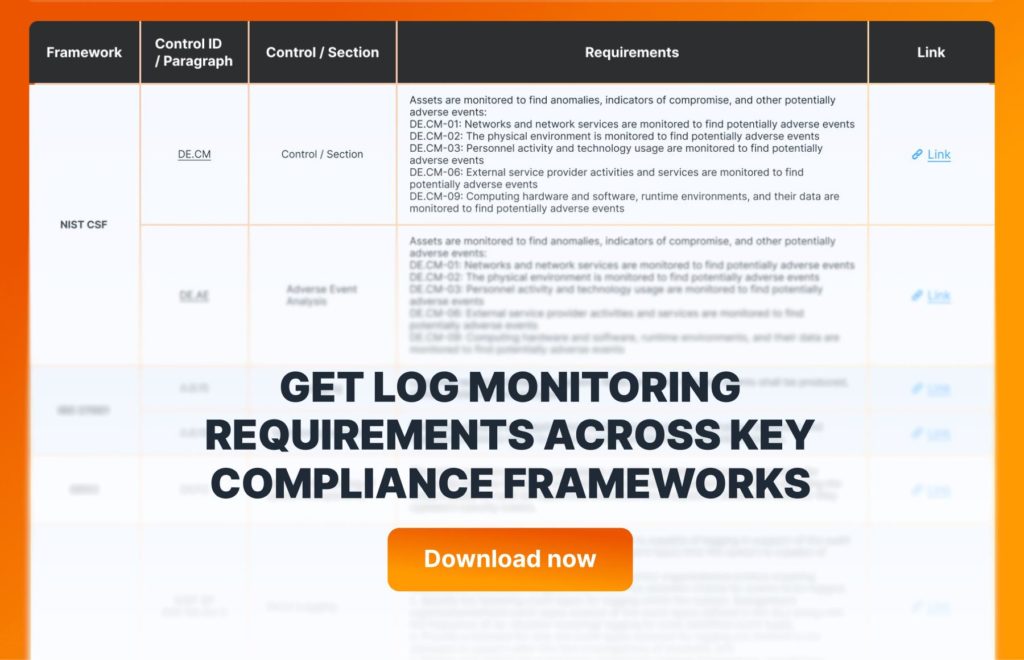
Your list of log monitoring requirements
We’ve made it easy for you with a downloadable table of the major compliance frameworks. It includes:
- Control IDs and sections for quick lookup
- Requirements to explain what’s needed
- Links to the regulations to save you time
This table is designed to save you time digging through documents and provide a clear path to compliance and security.

Log monitoring challenges
Let’s be honest: despite decades of log monitoring experience, businesses still use outdated approaches and legacy tools. Here are the challenges in log monitoring:
- Complexity. IT environments generate huge and complex log data, so you need more powerful tools to monitor it effectively. Storing large amounts of data is expensive, especially as retention periods grow.
- Log volumes and formats expand. Standardizing and analyzing data is difficult and requires a lot of resources.
- Legacy data silos increase cost and inefficiency; log monitoring is not as effective as a centralized system.
- Outdated/amateur approaches are useless for collecting, examining, and asking for logs, and log volume growth doesn’t make it any easier.
Tired of Log Alerts? Let Our SOC Experts Handle the Noise for You


How to build a security-first log monitoring strategy
When considering log management and 24/7 log monitoring, every organization has unique needs—but the goal is the same: reliable, round-the-clock security. Whether you go in-house or outsource, here are the main considerations from a security perspective that will help you decide.
1. Cost efficiency vs. control
- In-House: For companies with high budgets, managing log monitoring in-house can seem appealing. It offers control over data, team management, and custom setups. However, this control comes at a price—salaries for an experienced security team (often $1-2 million annually), plus significant setup costs for tools like SIEM (Security Information and Event Management). Hidden costs, such as employee burnout and turnover from round-the-clock shifts, can add security risks and reduce efficiency.
- Outsourced: SOC as a service offers affordable access to security expertise without the need for full-time hires. Most providers offer flexible, scalable pricing, usually based on data volume, making it an accessible choice for businesses of all sizes. Instead of an upfront investment, you’re paying predictable monthly fees and scaling the service as your needs grow.
2. 24/7 Threat detection and response
- In-House: Building an internal team capable of handling 24/7 monitoring is demanding. While shifts ensure coverage, organizing constant staffing can lead to fatigue and missed detections. Despite high costs, companies often face challenges in maintaining rapid, effective threat response due to these operational strains.
- Outsourced: Managed SOC providers specialize in continuous monitoring and have a team ready around the clock. They detect and address incidents quickly, using pre-built infrastructure to catch issues in real time. With automated alerts, you get immediate notifications, keeping your response team focused on core tasks while reducing risks from unmonitored threats.
3. Scalability and adaptability
- In-House: An internal team can be challenging to scale as your data volume increases. Adding staff or investing in new infrastructure can take time, and unexpected growth may strain existing resources. Without proper scaling, security can become vulnerable as the system grows.
- Outsourced: With SOC as a service, scalability is built-in. Outsourced providers adapt quickly to changes, whether your data grows or compliance needs shift. They handle the scaling on their end, so you don’t face delays or resource constraints when expanding your log monitoring coverage.
4. Compliance and expertise
- In-House: Keeping up with the latest compliance standards requires specialized expertise and ongoing training. For companies handling sensitive data, compliance with standards like GDPR, HIPAA, and PCI DSS is non-negotiable. While an in-house team can meet these standards, training costs and compliance gaps add to the burden.
- Outsourced: Outsourced SOC providers are experts in regulatory compliance and stay updated on requirements for industries like finance, healthcare, and retail. Outsourcing offers access to professionals who ensure your logs meet the necessary standards, reducing your compliance workload while protecting sensitive data.
Log management and SIEM
SIEM (Security Information and Event Management) systems are powerful tools that go beyond basic log management, combining log collection with advanced event analysis and threat detection. But having a SIEM is only the beginning. Setting it up, maintaining it, and fine-tuning it require serious expertise. Even with a high-end SIEM, managing it in-house is challenging. Without trained specialists to interpret reports, manage dashboards, and handle the constant stream of alerts, a SIEM can easily become overwhelming instead of protective.
This is where a managed SIEM service can make a difference. By handling setup, fine-tuning, and 24/7 monitoring, a managed service ensures your SIEM works as it should. With professionals interpreting alerts, reviewing reports, and covering shifts around the clock, a managed SIEM helps you maximize security without the weight of in-house management.
Let us make your SIEM work harder
UnderDefense: Way beyond simple log monitoring
UnderDefense goes beyond log monitoring and management. With our managed SOC and UnderDefense MAXI 24/7 threat detection and response platform, we offer enterprise-grade security at a fraction of the cost of building an in-house SOC. Starting at just $11 per asset per month, we deliver real-time monitoring and response across cloud and on-prem environments.
Our solutions scale with your business. During onboarding, we will consolidate and tune tools to reduce alert noise by over 82% so your team can focus on real threats. UnderDefense doesn’t just react to incidents—we prevent them, providing detailed reports to give you full visibility into your security. You get AI and automation, plus a dedicated SOC team. We help you reduce risk, speed up response, and reduce ops.
FAQ
1. What are the best log monitoring tools?
Top log monitoring tools include Splunk, Elastic Stack, Datadog, and UnderDefense MAXI. UnderDefense MAXI is a security automation platform backed by a 24/7 expert team, providing proactive, personalized threat defense and continuous log monitoring to keep your digital ecosystem secure.
2. What are log monitoring use cases?
Common use cases include detecting security threats, ensuring regulatory compliance, troubleshooting system issues, and improving operational efficiency.
3. What are log monitoring best practices?
What are log monitoring best practices?
Best practices include centralizing logs, setting up real-time alerts, regularly reviewing logs for anomalies, and implementing strict access controls.
4. What is centralized logging?
Centralized logging consolidates logs from multiple sources into one platform, making it easier to analyze, secure, and manage log data effectively.
5. How do you choose the best log monitoring tool?
Consider factors like scalability, ease of integration, alerting capabilities, compliance needs, and the level of automation required.